Reducing Attack Surface: A Keyless Approach to Client-Side Reverse Geocoding
bigdatacloud November 25, 2025
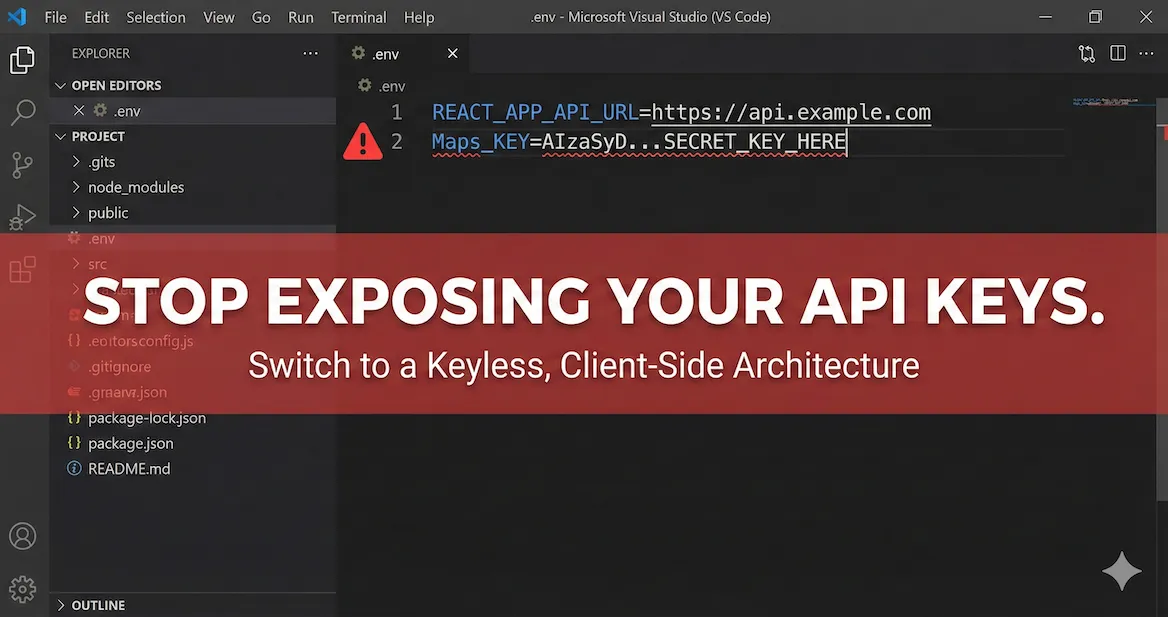
Exposing third-party API credentials in client-side JavaScript introduces unnecessary risk into application architecture. While controls like HTTP referrer restrictions offer partial mitigation, they are brittle to configure across multi-stage deployment environments (local, staging, production) and do not fully prevent quota theft or abusive request replaying.
Furthermore, robust geolocation implementation requires complex fallback logic—attempting device-level location (GPS) first, then reverting to network-level location (IP) if permissions are denied. Managing disparate APIs for these two methods introduces significant frontend complexity and technical debt.
This post outlines an alternative architectural approach using BigDataCloud’s keyless client-side API, which consolidates location services and eliminates the need for frontend secrets management.
1. Improving Security Posture via Secret Elimination
The standard pattern for client-side geolocation involves either exposing an API key in the frontend bundle or engineering a backend proxy solely to inject credentials into requests. Both approaches add operational overhead.
BigDataCloud’s client-side endpoint is unauthenticated by design. It relies on origin-based fair use policies rather than secret keys to manage traffic.
By removing the requirement for an API key on the client, you eliminate an entire class of security risks related to credential leakage and misconfiguration. There is zero attack surface related to stolen keys because there are no keys to steal.
2. Architectural Simplification: Unified Fallback Logic
A production-grade location service requires a waterfall approach:
- Attempt to acquire high-precision coordinates via the browser's
navigator.geolocationAPI. - Catch permission denial or timeout errors.
- Fallback to an IP-based geolocation service as a secondary measure.
Implementing this with traditional providers often requires managing two separate service integrations, two sets of error handling logic, and, most critically, writing adapters to normalise disparate JSON output schemas.
The BigDataCloud endpoint abstracts this complexity. A single call handles the entire waterfall. It attempts to resolve high-precision coordinates if provided; if not, it transparently falls back to IP geolocation.
Crucially, the output JSON schema is identical regardless of the resolution method. This significantly reduces frontend code complexity and maintenance burden.
3. Sustainability: The Economics of "Free"
A common question from engineering teams is how a service without hard quotas or billing can be sustainable. Is this a temporary loss-leader?
The model is based on a technical data exchange, not a marketing promotion.
BigDataCloud maintains one of the industry's most accurate IP geolocation datasets. To achieve this, we require continuous ground-truth validation to map IP addresses to physical locations. When your application uses our client-side API (with user consent), it effectively acts as a verification node. The precise GPS coordinates provided by the client allow us to validate and refine the routing data for that specific IP network. Why is BigDataCloud's Reverse Geocoding API Free?
- You receive: Enterprise-grade, unlimited reverse geocoding without managing keys or bills.
- We receive: Real-time signal validation that improves our core paid product (Server-Side IP Geolocation).
This symbiosis ensures the model is commercially sustainable and permanent. It removes the "too good to be true" factor—it is simply an efficient data feedback loop.
4. Operational Predictability and Cost Control
Many geolocation services utilise hard rate limits or tiered overage pricing, which introduces operational risk and unpredictable costs during traffic surges.
This service operates on a fair-use basis specifically for client-side calls. This model decouples cost from volumetric traffic spikes, ensuring service availability and predictable operational expenditure as the application scales.
5. Data Privacy and Compliance Considerations
Authenticated requests to standard third-party geocoding providers inherently link a user's IP address with the customer's API identity. This creates metadata tying specific IP addresses to specific types of applications (e.g., linking an IP to a healthcare application ID).
A keyless architecture decouples the location request from the application's identity. The provider processes the IP anonymously without tying it to a specific customer account. This supports data minimisation principles essential for compliance frameworks like GDPR and the Privacy Act.
Implementation Comparison
The following demonstrates the reduction in complexity when moving from a traditional multi-provider setup to a unified, keyless approach.
Traditional Architecture (High Complexity)
Requires credential management, multiple error handlers, and schema normalisation.
// 1. Attempt browser geolocation
navigator.geolocation.getCurrentPosition(
(pos) => {
// 2. Call Google Maps API (Requires exposed key or backend proxy)
// 3. Parse Google's address_components schema
},
(err) => {
// 4. Catch permission error
// 5. Call separate IP Geolocation API (Requires different key)
// 6. Parse different JSON schema
// 7. Normalise data to match Google's format for application consistency
}
);
Keyless Unified Architecture (Low Complexity)
Single endpoint, no secrets, unified schema.
// Single call handles GPS/IP fallback internally.
const resolveLocation = async () => {
// No API key required in the request URL
const url = `https://api.bigdatacloud.net/data/reverse-geocode-client`;
const response = await fetch(url);
const data = await response.json();
// Schema is consistent regardless of resolution method (GPS or IP)
console.log(`Resolved location: ${data.city}, ${data.countryName}`);
}
Conclusion
Switching to a keyless, unified reverse geocoding API reduces operational overhead by eliminating frontend secrets management, simplifying codebase architecture through a single-schema fallback mechanism, and improving the overall security and privacy posture of the application.